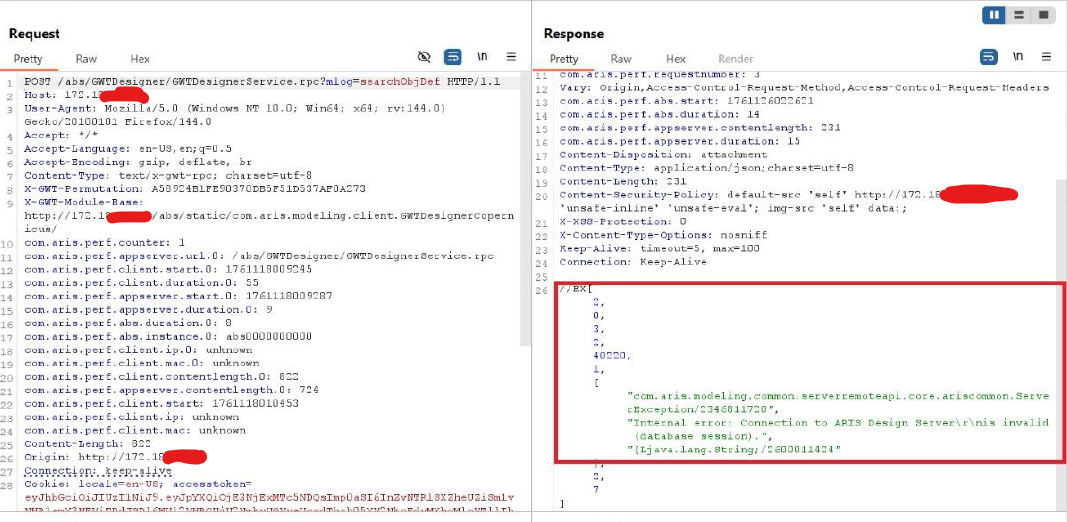
We're doing DAST using Burp Suite in our ARIS and we've got some medium severity vulnerability with the issue name: Information Disclosure. And the details are below:
Issue Description
Some browsers, including Internet Explorer, contain built-in filters designed to protect against cross-site scripting (XSS) attacks. Applications can instruct browsers to disable this filter by setting the following response header:
This behavior does not in itself constitute a vulnerability; in some cases XSS filters may themselves be leveraged to perform attacks against application users. However, in typical situations XSS filters do provide basic protection for application users against some XSS vulnerabilities in applications. The presence of this header should be reviewed to establish whether it affects the application's security posture.
Proof Of Concept
Request
Response
Validation Manual
Affected URL
http://172.18*.***.**/abs/GWTAttrEditing/GWTAttrEditingService.rpc
http://172.18*.***.**/abs/GWTDesigner/GWTDesignerService.rpc
Is there any configuration that we can use to pass the vulnerability?